Based on my LinkedIn feed, the biggest story of the week in security-land is the U.S. SEC filing charges against SolarWinds and its CISO, Timothy Brown, for fraud and control failures.
Unsurprisingly, this has made waves in security circles. Some people are seemingly exasperated about how this sets a dangerous precedent for CISOs and whether the job is even still worth doing, with the possibility of charges hanging over their head.
One element I would like to highlight is that it’s a little worrying how many CISOs, who are supposed to be C-level executives, don’t realise that the “control failures” above are financial reporting ones, not cyber security ones. This is not to mention that they don’t realise that misconduct in a C-level role is likely to have consequences.
A Bigger Issue in Cybersecurity
However, what struck me most about the news is something else entirely. It’s something much bigger, something of cataclysmic importance to our industry, and something I saw no one else mention.
It’s the following line in the SEC’s statement:
… a September 2020 internal document shared with Brown and others stated, “the volume of security issues being identified over the last month have outstripped the capacity of Engineering teams to resolve..."
The fact that this organisation was identifying more security issues than it could address might be shocking to some people. It’s even more shocking if you consider that, for every issue identified, there are likely several more that haven’t been.
The reality is that this is standard fare in Information Security. It’s something many of us wear as a badge of honour; we are taking on an impossible fight to protect the business.
There’s just one problem with that: it’s an impossible fight. And doing it at the business’ expense is hardly honourable.
Security spending has increased dramatically over the last 20 years. Not just in absolute terms, but as a percentage of organisations’ resources. And yet, the number of breaches and incidents keeps increasing, exponentially by some accounts.
As businesses and [hopefully] security leaders start realising this, they will have to come to a simple but very hard conclusion: our current approach to security is not sustainable.
Or rather...
Treating Security Primarily as a Risk Management Function Is Unsustainable
Most industries apply quality management principles to address root causes of defects and incidents. This drives cumulative improvements (reductions) as each root cause is eliminated until a baseline is reached. Eventually, the cost of further investment in quality and rectification of root causes will cost more than just leaving the defects in place.
It’s at that time that operational risk management activities take over; to mitigate the impact of risks that are too unpredictable or low in frequency or impact to be worth eliminating more proactively.
The problem I see in the security space is that we define our role as one of Risk Management. This means we very rarely reduce the number of risks in the first place. We just ramp up capacity to try and keep up instead.
I recently saw a presentation with a very simple slide. It featured three boxes like this:
[Threat] → [Vulnerability] → [Impact]
We spend most of our time, effort, and spending on stopping threats from exploiting our vulnerabilities to avoid impacts to our business, and very little actually stopping vulnerabilities from occurring. Vulnerabilities without which the threats wouldn’t be very threatening, and impacts couldn’t occur.
This means that, as our organisations grow, and as we build more software, we have more systems and applications that need maintenance, and the number of vulnerabilities increases. This is because we’ve done little to stop them, because we’re too busy mitigating the impacts.
The irony is that many of the vulnerabilities are the same, yet we keep reintroducing them. And we keep ‘risk-managing' them.
In the graph below we see the number of vulnerabilities identified each year. Our failure to address many of these means that the cumulative burden is getting exponentially heavier each year.

Source: Security Intelligence
However, the reality is much worse than this because the nature of these vulnerabilities is largely unchanged. If we look at the top 10 OWASP vulnerabilities for the last 20 years, they have changed little. We keep repeating known mistakes, and we focus on mitigating their impact instead of addressing the core problem.
Other Industries Largely Get It Right – Why Not Cybersecurity?
Imagine if the aviation industry kept repeating the practices or defects that led to air disasters in the past. Imagine they kept using the same components that have been identified as failing, causing aircraft to plummet to the ground, due to design flaws. Or that they’d build new components using the same approaches and designs that are known to fail. Or that they’d follow the same processes that have been proven to lead to oversights and dangerous issues. It would be outrageous, and trying to keep planes flying safely with operational risk management of those flaws would be financially crushing.
It just doesn’t work that way. They learn from what caused their incidents and apply changes as far upstream as possible to make sure they never happen again. They don’t merely ramp up reactive capacity in dealing with the risks.
And yet, we often ignore these proven common-sense approaches in security. They’re not limited to my software development examples either. It’s how systems are accessed, built, configured, provisioned, managed, maintained, and even the business process context in which they are used.
Also worrying is that, while we are engaged in this unwinnable cyber security arms race, attackers are increasingly bypassing the security function altogether by exploiting systems and business processes beyond the visibility of the typical IT Security function.
The statement about SolarWinds highlights a problem with how security is done today. But it’s in no way unique to them.
This is a race that we are losing, badly. No amount of investment - up to and including bankrupting our organisations with security spending - when taking the current approach will be able to keep up if future estimates are to be believed.
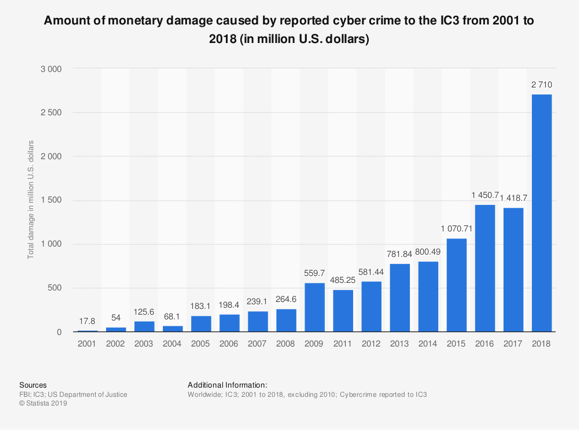
Source: Research gate
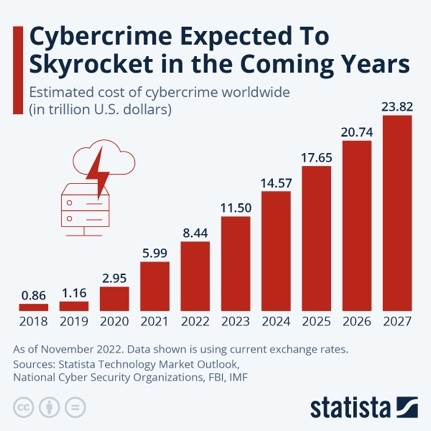
Source: Statista
Cybersecurity Transformation Is Needed
We must change our approach. We must fix our increasing fragility rather than merely guarding it against an ever-increasing number of risks.
I know from my experience as a CISO that it is possible to reduce the number of issues we must deal with in the security team by improving things far upstream, leading to reduced security costs and a variety of additional business benefits. However, this requires a very different approach to the status quo.
It requires a more holistic view, more influence, and different capabilities and toolsets, but it is a journey that isn’t just worth taking, it’s necessary.
How we help take customers on this transformational journey is something that has been getting a lot of thought over the last few months at CDW within the Office of the CTO. We want to help our customers achieve the outcome of being more secure, not forever needing more security.
We look forward to sharing stories of our progress and our successes.
We hope you’ll be one of them.
Contributors
-
 Greg Van Der Gaast
Greg Van Der GaastSecurity Advisor to CDW







